Difference between revisions of "DC-9"
Jump to navigation
Jump to search
(edit height and width - nmap scan pic) |
|||
| Line 15: | Line 15: | ||
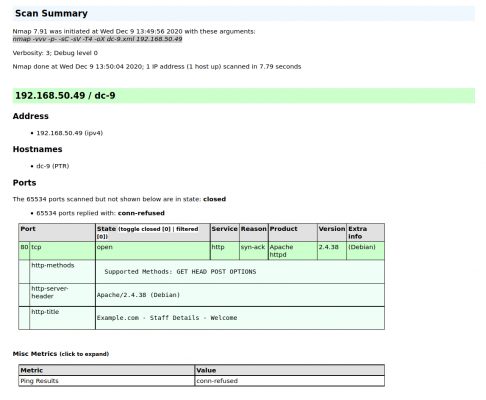
nmap -vvv -p- -sC -sV -T4 -oX dc-9.xml 192.168.50.49 && xsltproc dc-9.xml -o dc-9.html | nmap -vvv -p- -sC -sV -T4 -oX dc-9.xml 192.168.50.49 && xsltproc dc-9.xml -o dc-9.html | ||
| − | <gallery> | + | <gallery widths="500" heights="400"> |
File:Dc-9 nmap scan.png | File:Dc-9 nmap scan.png | ||
</gallery> | </gallery> | ||
Revision as of 19:47, 12 December 2020
Description
"DC-9 is another purposely built vulnerable lab with the intent of gaining experience in the world of penetration testing.
The ultimate goal of this challenge is to get root and to read the one and only flag.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools."
You can download the machine at https://www.vulnhub.com/entry/dc-9,412/
Enumeration
nmap -vvv -p- -sC -sV -T4 -oX dc-9.xml 192.168.50.49 && xsltproc dc-9.xml -o dc-9.html